Enhancing IoT Security with RemoteIoT VPC SSH on Raspberry Pi provides a robust solution for managing and accessing IoT devices from anywhere in the world. As the Internet of Things (IoT) continues to expand, the need for reliable and secure remote access becomes increasingly critical. The Raspberry Pi, known for its affordability and versatility, has emerged as a top choice for IoT enthusiasts and professionals alike. By integrating Raspberry Pi with RemoteIoT's Virtual Private Cloud (VPC) and Secure Shell (SSH), users can create an environment that prioritizes security and flexibility. This setup allows users to manage their IoT devices efficiently while maintaining the highest standards of protection.
In today's rapidly evolving digital landscape, having secure remote access is no longer optional—it's essential. Whether you're a developer working on complex IoT projects, a system administrator overseeing multiple devices, or a hobbyist exploring smart home technologies, secure and efficient remote access is indispensable. The RemoteIoT VPC SSH Raspberry Pi combination offers a comprehensive solution that balances security, ease of use, and adaptability. This makes it an excellent choice for a wide range of applications, catering to both beginners and experienced users alike.
This detailed guide will walk you through the entire process of setting up and utilizing RemoteIoT VPC SSH with Raspberry Pi. From grasping the foundational concepts to implementing advanced security measures, we'll cover every aspect of this dynamic partnership. Whether you're just starting or already familiar with remote access solutions, this article will provide valuable insights and actionable steps to help you maximize the potential of your setup.
Read also:Exploring Hdhub4u A Comprehensive Guide To Hindi Movie Downloads
Table of Contents
- Understanding RemoteIoT VPC
- SSH Basics and Security
- Setting Up Raspberry Pi for Remote Access
- Integrating RemoteIoT with Raspberry Pi
- Advanced Security Measures
- Real-World Use Cases
- Troubleshooting Common Issues
- Performance Optimization Techniques
- Future Developments in Remote Access
- Conclusion and Next Steps
Exploring RemoteIoT VPC
RemoteIoT's Virtual Private Cloud (VPC) creates a secure and isolated environment for managing IoT devices. Unlike traditional public cloud services, a VPC offers dedicated resources and advanced security features tailored for handling sensitive IoT data. The VPC architecture establishes a virtual network that separates your devices from other users' resources, ensuring enhanced privacy and greater control over your infrastructure.
Key Features of RemoteIoT VPC
- Private IP addressing for increased security
- Customizable network configurations to suit specific needs
- Integrated firewall and access control for robust protection
- Automatic scaling capabilities to adapt to growing demands
- Seamless integration with existing systems for a unified approach
Advantages for IoT Projects
The RemoteIoT VPC delivers numerous benefits for IoT projects. It provides a stable and secure platform for device communication, significantly reducing the risk of unauthorized access. The scalability of the VPC allows for effortless addition or removal of devices as your project expands. Additionally, the integrated monitoring tools assist in tracking device performance and identifying potential issues before they escalate.
Understanding SSH and Enhancing Security
Secure Shell (SSH) is a cryptographic network protocol that facilitates secure access to remote systems. When combined with RemoteIoT VPC and Raspberry Pi, SSH becomes an indispensable tool for managing IoT devices securely. This protocol encrypts all data transmitted between your local machine and the remote device, safeguarding sensitive information from interception.
Setting Up SSH on Raspberry Pi
To activate SSH on your Raspberry Pi, follow these straightforward steps:
- Launch the Raspberry Pi configuration tool
- Proceed to the "Interfaces" tab
- Enable SSH
- Set up strong authentication methods for added security
- Configure SSH keys to enable passwordless login
Strengthening SSH Security
- Use key-based authentication rather than passwords for enhanced protection
- Implement IP whitelisting to restrict access to trusted IPs
- Change the default SSH port to minimize brute-force attack risks
- Enable two-factor authentication for an additional layer of security
- Regularly update SSH software to patch vulnerabilities
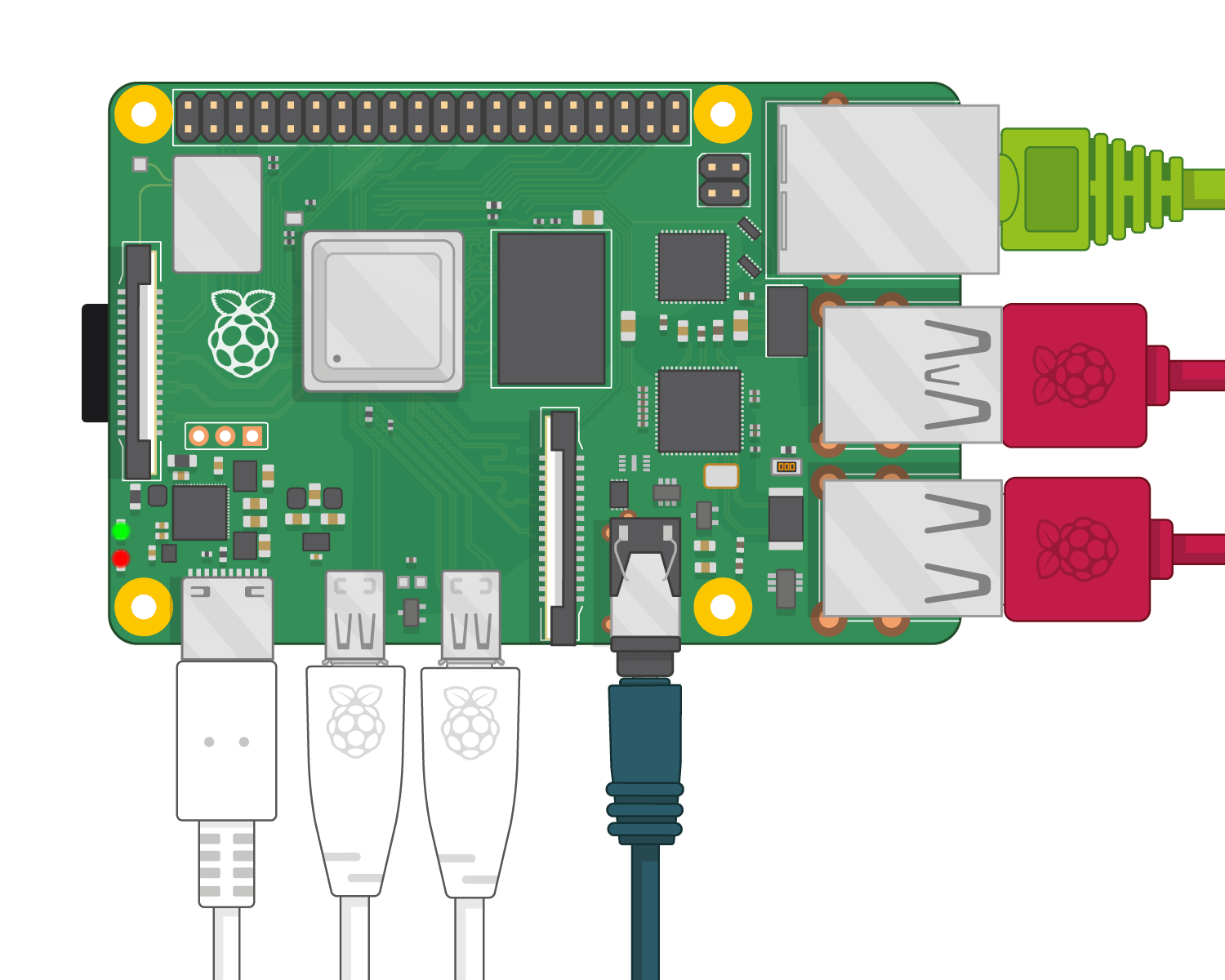
Preparing Raspberry Pi for Remote Access
Getting your Raspberry Pi ready for remote access involves several essential steps. Start by ensuring your device is updated to the latest version of Raspberry Pi OS. This ensures access to the newest security patches and features. Next, configure the network settings to maintain stable internet connectivity, which is crucial for consistent remote access.
Optimizing Raspberry Pi for Remote Management
Follow these steps to fine-tune your Raspberry Pi for remote management:
Read also:Uday Chopra A Multifaceted Journey In Bollywood
- Update the operating system and all packages to the latest versions
- Set a static IP address to avoid connection disruptions
- Configure the hostname for easier identification within your network
- Install necessary monitoring tools to track system health and performance
- Set up automatic backups to preserve important data
Recommended Software for Enhanced Functionality
- Fail2Ban for effective intrusion prevention
- UFW (Uncomplicated Firewall) for simplified firewall management
- Logwatch for comprehensive system monitoring
- htop for real-time resource monitoring
- Cron for scheduling automated tasks
Connecting RemoteIoT with Raspberry Pi
Integrating RemoteIoT with your Raspberry Pi involves a series of steps that establish a secure and efficient connection between your device and the cloud infrastructure. This process begins with creating a RemoteIoT account and configuring your VPC settings to align with your Raspberry Pi requirements.
Step-by-Step Integration Process
- Create a RemoteIoT account and configure your VPC
- Install the RemoteIoT agent on your Raspberry Pi
- Adjust VPC network settings to meet Raspberry Pi specifications
- Set up secure SSH tunneling through RemoteIoT infrastructure
- Verify connectivity and test remote access functionality
Configuration Parameters
| Parameter | Recommended Value | Description |
|---|---|---|
| VPC Subnet | 10.0.0.0/16 | Private IP range for VPC |
| SSH Port | 22 (default) | Port for secure shell access |
| MTU Size | 1500 | Maximum transmission unit for network packets |
| Timeout | 300 seconds | Connection timeout setting |
Implementing Advanced Security Protocols
While basic security measures are fundamental, incorporating advanced security protocols is critical for safeguarding your RemoteIoT VPC SSH Raspberry Pi setup. These measures protect against sophisticated attacks and maintain the integrity of your IoT infrastructure.
Multi-Layer Security Implementation
- Deploy intrusion detection systems (IDS) to monitor and respond to threats
- Implement network segmentation to isolate critical components
- Utilize encrypted storage for safeguarding sensitive data
- Regularly rotate SSH keys to reduce the risk of key compromise
- Monitor and analyze system logs for suspicious activities
Security Best Practices
Adhere to these best practices to fortify your system's security:
- Perform regular security audits to identify vulnerabilities
- Implement role-based access control (RBAC) for granular permissions
- Use strong, unique passwords for all accounts to prevent unauthorized access
- Enable automatic security updates to stay protected against emerging threats
- Restrict root login access to minimize risks associated with privileged accounts
Practical Applications Across Industries
The RemoteIoT VPC SSH Raspberry Pi combination finds utility across various sectors and scenarios. From enhancing smart home automation to supporting industrial IoT solutions, this setup provides a versatile platform for implementing secure remote access solutions.
Smart Home Automation
In smart home environments, this setup empowers homeowners to remotely control and monitor devices securely. Whether managing smart locks or regulating HVAC systems, the integration of RemoteIoT and Raspberry Pi offers a dependable platform for home automation projects.
Industrial Applications
- Remote monitoring of manufacturing equipment for predictive maintenance
- Secure access to industrial control systems for operational efficiency
- Real-time data collection and analysis for informed decision-making
- Remote maintenance and troubleshooting to reduce downtime
- Energy management and optimization for cost savings
Addressing Common Issues
Even with meticulous setup and configuration, users may encounter issues when working with RemoteIoT VPC SSH Raspberry Pi. Understanding common problems and their solutions can help minimize disruptions and ensure smooth operation.
Frequent Connection Challenges
- Network connectivity issues due to unstable internet connections
- Firewall configuration errors preventing access
- Authentication failures from incorrect credentials or misconfigured keys
- Port forwarding problems causing connection timeouts
- Software version conflicts leading to incompatibility
Troubleshooting Procedures
- Verify network connectivity by using the ping command
- Check firewall rules and configurations for potential blockages
- Validate SSH key configurations to ensure proper authentication
- Review system logs for error messages to pinpoint issues
- Test the setup in different network environments to isolate the problem
Maximizing System Performance
Optimizing the performance of your RemoteIoT VPC SSH Raspberry Pi setup involves implementing strategies that enhance speed, reliability, and resource utilization. These techniques ensure your system operates efficiently, even under demanding conditions.
System Optimization Techniques
- Implement caching mechanisms to reduce repetitive data retrieval
- Optimize network settings for faster and more reliable communication
- Use lightweight applications to minimize resource consumption
- Enable compression for data transfer to improve efficiency
- Regularly clean temporary files to free up storage space
Resource Management Strategies
Effective resource management is vital for maintaining peak performance:
- Monitor CPU and memory usage to identify bottlenecks
- Set up automatic resource scaling to adapt to varying workloads
- Implement load balancing to distribute tasks evenly
- Use efficient data storage solutions to enhance data handling
- Regularly update system components to incorporate improvements and fixes
Emerging Trends in Remote Access Technology
The field of remote access technology is advancing rapidly, with new innovations continuously emerging. Staying informed about these trends can help you leverage cutting-edge solutions for your RemoteIoT VPC SSH Raspberry Pi setup.
Emerging Technologies
- Quantum-resistant encryption methods for long-term security
- AI-powered security systems for proactive threat detection
- Edge computing integration for reduced latency and improved performance
- Zero-trust security models for enhanced protection against unauthorized access